Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
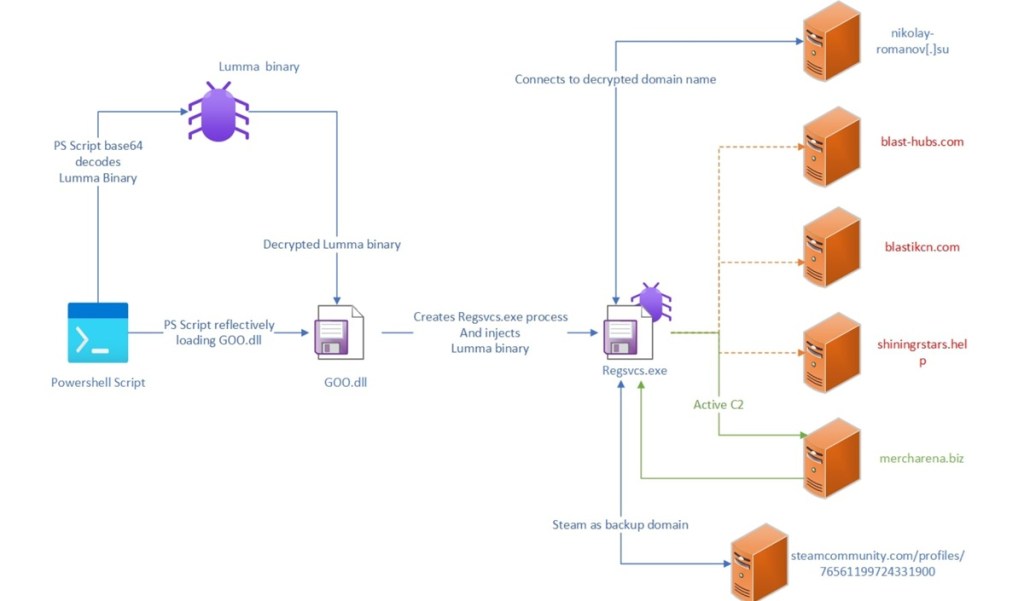
[ad_1]
During regular active threatening hunting, Trellix Advanced Research Center been defined in full infostaller An example of malicious software is written in the game targeted pass code.
During the additional investigation, the team in Trellix revealed that in the telegram since late December 2024. Trellix, Niranjan Hegde, Vasantha Lakshmanan reported a report entitled “Demystify Mif Stealeri” written by Ambasankar and Abars.
Infostealers is a kind malicious software There is a functionality to collect computer systems and collect passwords, cookies, credit card information, autocomplete data, scanning history and file upload date.
A pattern was written Rust The harmful program is written using a special programming language known as “pass”, which is a “pass”, which is a general programming language, which is written in the previous malware c / C ++. It is more widely understood and analyzed by threatening researchers and defenders.
The advantage of using Rust is the maximum platform support in terms of operating system, which can be executed by this harmful program, expanding the exposure to the victims.
Myth Stealer is the name of the pass-based malware that is actively promoted in the telegram, offers advanced features that make it very attractive to cyber crimes. The group behind this harmful program does not set up game sites; On the contrary, they submit a subscription to a malicious program. Then the attackers who subscribe to this particular malware are setting up game sites.
Initially, it was offered for a test for free and then turned into a subscription-based model. The investigation revealed that this info was distributed through various fake game sites. When executed, the malware shows a fake window to make it legal while changing and implementing a malicious code in the background.
Infostealer produces sensitive information, including both slimming and chrome-based browsers, passwords, cookies and autofill data. Ayrıca, FileNames və istifadəçi adı istifadə edərək simli obfuscation və sistem yoxlamaları kimi anti-anti-anti-anti-anti-anti-anti-anti-anti-antioniklər.
The authors of harmful software update the theft code regularly to avoid detection and display capture and display capture capability and clipboard abduction.
This article was made in late December 2024. The telegram channel was used to share updates on malware stealing myths. An organized team, based on the activity on the channel, developed and maintained.
After closing the first telegram channel, operators created a new group to share harmful software updates. Emphasizing zero detection rates in VirusTotal, this group regularly announces new versions. Users must reset the latest updates to integrate their structures.
Currently, the malware is offered based on weekly and monthly subscriptions. Purchase using Crypto-Currency and Razer Gold. In addition, they have protected a channel called “Myth and Market Place”, which provides the statements of these theft users and used this theft. Currently connected by the telegram.
In another case, under a cheater program called “DDTRACE KRX Ultimate Cracts” opened an actor who sent a link to the malicious RAR file in an online forum. To create reliability within the forum community, the actor created a virusotal contact that shows zero detection at that time.
The myth stole is presented as a game of scams in an online forum. According to our investigation, malicious programs have developed over a period of time. Initially, when distributed as a free trial version, it has stolen information from applications only.
After passing a subscription-based model, it was sold with additional functions, taking the screenshots, taking screenshots, taking the screenshot, the team continues to update and update the code to ensure that the malware is not detected in the virusotal.
These updates include libraries used to update a fake window, update communication with C2 Server, communication in the following sections, etc.
Currently, the harmful program is a 64-bit example of a 64-bit sample, which is a bundling and executing loader who decodes the stolen component. After the victim’s machine is successfully loaded in the victim’s machine, the loader with a fake window shows a fake window to the user.
These fake windows are used to deceive by thinking that a victim is a legitimate application. Uses the Pass Chest: a native-window-GUI or local_dailog to create and show fake window.
Some of the fake windows displayed by the loader. Although the fake window is shown the victim, using the PAS Chest, using the Pas Chest, using the Pass Chest or using the choir or AES encryption decrypts. In recent versions, the loader uses a special algorithm to open the theft component.
The newly emerging pass-based infostealer continues to develop in the versions of myths, gradually becomes difficult for the final point solutions to detect it. Features such as string obfuscation, hidden C2 communication and fake window, reflect the advanced deviation technique of danger actors.
The consistent development and development of the myth of the myth aims to be ahead of security protection of attackers, creating a serious and durable risk for users, especially through counterfeit game sites.
[ad_2]
Source link