Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Join our daily and weekly newsletters for the latest updates and exclusive content in the industry’s leading AI coverage. Learn more
Enterprise employees are eager to take advantage of AI tools – do not like employers. This is not acknowledged, acting as a shadow AI, increases sharply: up 96% of the work Workers with AI are through non-corporate accounts. Unidentified or harmful, this can leak the highly sensitive and property information of an enterprise.
Security platform Cyberhaven This problem can solve this problem by tracking the offspring or information of information between different users and end points. The company has special great generation models (LLLS) for this position, and the next generation of the platform is to stop the shadow AI and be the most dangerous of flagged events Linea AI.
“This is a generation of this generation: You understand where all the different end points you have, all your users,” Badge Doshi, Cyberhaven’s information within the General and Development Worker.
According to the analysis of workflows of Cyberhaven, the use of AI has increased 485% 2023 and 2024 shares sensitive information between 2024: about 83% of legal documents and the source code, research and development materials, share employees with AI and employees’ non-corporate AI accounts.
To help prevent this unauthorized use and protect sensitive company information, Linea uses an Limelic Individual enterprise trained to actual enterprises. Equipped with computer vision and multi-modal AI, you can analyze the information from images, screenshots, technical diagrams and other materials. The feature of a new “Linea AI decision” is evaluates policy violations and measurement violations and dimensions to reduce the security center (SOC) warning.
“Thus, like the Great Language Model (LLM), which predicts the next word, we predict what the next action will happen,” Doshi explained.
Cyberhaven sees that as a result, customers see a 90% reduction in the events that require customers’ hand review and 80% decrease in the 80% reduction in information security. The company’s instruments can detect 50-PY plus risks in the month, which are not detected by traditional means.
“Cyberhaven said,” Said Prabhath Karanth, Cso and Family Finance Application that our data moves and how the information moves within the organization, “Said Prabhath Karanth, CSO and Family Green light. “Now we have a single platform that only traditional data loss prevention (DLP) and Insider’s risk management understands how people use information in our whole organization.”
Doshi explained that traditional approaches are directed to sample adaptation – Identify network and data samples to detect anomalies and vulnerabilities – CyberHaven implements content and context. Its platform explores information and provides context in the context based on lineage tracks.
“So, if you download something, you send it to me, I send him to five others, I send it to five others – this is a generation,” Doshi explained.
Cyberhaven’s offer is equipped with border AI models and a transformer neuron network architecture. Analyzing the most valuable information of an enterprise and “to reach a needle in the grass room”, a multi-stage search engine uses an extended generation (dwarf) engine.
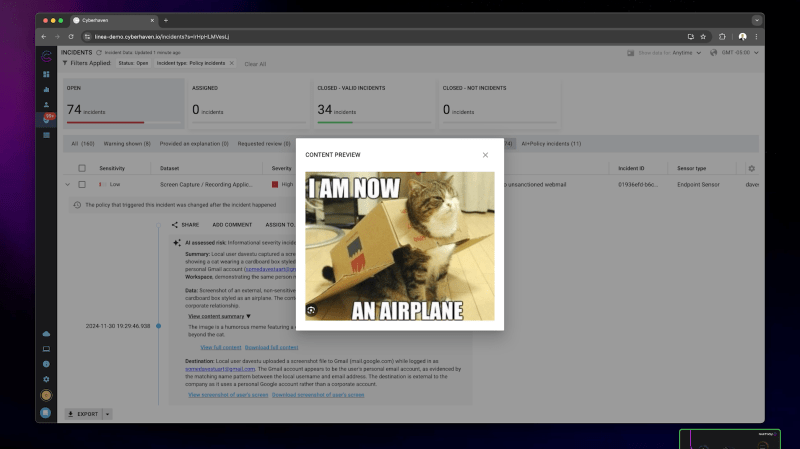
The platform performs a smart screenshot analysis with “continuous blind point” in data security. Blush.
Thus, for example, a security group to prevent a security group from leaving the company. There may be thousands, and this should pass a non-harmless cat meme or a screenshot that contains a product schematics.


“The disclosure, engineering designs, AI models, research data, product road maps, it is difficult to prevent, product paths, Arkeen.
Cyberhaven now receives cybershelf security, new autonomous, EU-power EU-power, the EU and the security teams decided to filter with information and user notes to help understand the violence of the incident. The platform understands screenshots, PDFs, source code and other digital materials and can provide context based on information generation, Doshi explained. Later, an event may also eliminate whether to be considered by human analysts.
“We are trying to predict the next action based on all historical knowledge: this is this bad event,” said Doshi. “We say the concept of this information because you really look at the information and understand the depth of the information.”
Arken explained that as if in the risk of insider, security teams are developed to create a high level of information on a high level (based on any number of factors).
“Let’s say I expand you, and 150 incidents were created today,” he said. “I’d be hand over to each of them, ‘It’s work as usual.’ It seems a little suspicious. ‘ ‘It looks really suspicious.’ After that, there are others for the passage of something else. The EU is the suspect to choose those who require an analysis or further analysis and can save all this time. “
For example, platform users can discover users who send users to private OneDrive or sync sensitive files to iCloud, Doshi. In addition, a harmful step is the workers who are out of a company and trying to get sensitive information.
“We can prevent users or users from downloading this public LLMS in real time,” Doshi said. “We can notify them and we can notify them.
DailyPay, in turn, was able to reduce the MTRT for 65%, as the digestible AI summary, Arkeen said. Typical data loss prevention (DLP) tools require many personnel resources to gain such visibility type.
Netskope, DTEX systems and other DLP providers, including the next DLP, but doubled in Cyberhaven due to the extent of the information generation strategy. Said it was different from something done in the industry.
“This is a lot of time related to the escalation and trigative and prevention,” Arkeen said. “Linea AI consistently determines the risks that traditional systems completely miss.”